DKMS
|
Size: 2428
Comment:
|
← Revision 19 as of 2018-06-26 19:53:49 ⇥
Size: 2627
Comment:
|
| Deletions are marked like this. | Additions are marked like this. |
| Line 3: | Line 3: |
| Following [[https://wiki.ubuntu.com/Spec/InstallingUnsignedSecureBoot|an UOS approved spec]], Ubuntu is checking module signing by default, on kernels 4.4.0-18.34, 4.4.0-21.37, 4.2.0-42.49, 3.19.0-65.73 and 3.13.0-92.139 onwards. You can read more details in this [[https://bugs.launchpad.net/ubuntu/+source/linux/+bug/1566221|bug in Launchpad]]. | Ubuntu is now checking module signing by default, on kernels 4.4.0-18.34, 4.4.0-21.37, 4.2.0-42.49, 3.19.0-65.73 and 3.13.0-92.139 onwards. You can read more details in this [[https://bugs.launchpad.net/ubuntu/+source/linux/+bug/1566221|bug in Launchpad]]. |
| Line 11: | Line 11: |
| Simply install the package you need. Packages that make use of DKMS should prompt you to add new keys or disable Secure Boot, as appropriate for your system, and should do so automatically. | Simply install the package you need. Packages that make use of DKMS should prompt you to create a new Machine-Owner key (it will be done for you), and will guide you through the steps to enroll that key in your system's firmware. |
| Line 13: | Line 13: |
| == Method 2 - Disable Secure Boot from BIOS == 1. Enter BIOS setup 1. Disable secure boot 1. Save configuration 1. Reboot the system == Method 3 - Disable Secure Boot in shim-signed == 1. Open a terminal ('''Ctrl + Alt + T'''), and execute '''sudo update-secureboot-policy''' and then select '''Yes'''. {{attachment:update-secureboot-policy.png|align="left"}} |
== Method 2 - Disable Secure Boot in shim-signed == 1. Open a terminal ('''Ctrl + Alt + T'''), and execute '''sudo mokutil --disable-validation'''. |
| Line 23: | Line 16: |
| {{attachment:Enter_a_temporary_password.png|align="left"}} | |
| Line 25: | Line 17: |
| {{attachment:confirm_password.png|align="left"}} | |
| Line 36: | Line 27: |
| You can still enable Secure Boot in shim-signed again. Just execute '''sudo update-secureboot-policy --enable''' and then follow the steps above. | To re-enable Secure Boot validation in shim, simply run '''sudo mokutil --enable-validation'''. == Method 3 - Disable Secure Boot from BIOS == 1. Enter BIOS setup 1. Disable secure boot 1. Save configuration 1. Reboot the system == Manual method == You may also opt to sign modules yourself. To make this simple, you can use the command: '''sudo update-secureboot-policy --new-key''' To create a new MOK key to use for signing, then run the appropriate '''kmodsign''' command to sign your kernel module. After the module is signed, run '''sudo update-secureboot-policy --enroll-key''' to step through the enrollment wizard, or do the enrollment yourself by running '''sudo mokutil --import <your key>'''. |
DKMS modules need to be configured to work with UEFI Secure Boot
Ubuntu is now checking module signing by default, on kernels 4.4.0-18.34, 4.4.0-21.37, 4.2.0-42.49, 3.19.0-65.73 and 3.13.0-92.139 onwards. You can read more details in this bug in Launchpad.
Because of those changes, DKMS modules will not work on systems with Secure Boot enabled unless correctly configured.
In order to make DKMS work, Secure Boot signing keys for the system must be imported in the system firmware, otherwise Secure Boot needs to be disabled. There are several methods to configure your system to properly load DKMS modules with Secure Boot enabled.
Method 1 - Install the DKMS package you need
Simply install the package you need. Packages that make use of DKMS should prompt you to create a new Machine-Owner key (it will be done for you), and will guide you through the steps to enroll that key in your system's firmware.
Method 2 - Disable Secure Boot in shim-signed
Open a terminal (Ctrl + Alt + T), and execute sudo mokutil --disable-validation.
- Enter a temporary password between 8 to 16 digits. (For example, 12345678, we will use this password later
- Enter the same password again to confirm.
- Reboot the system and press any key when you see the blue screen (MOK management
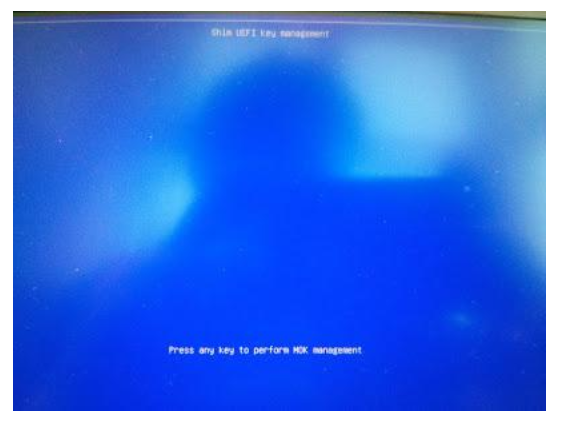
Select Change Secure Boot state
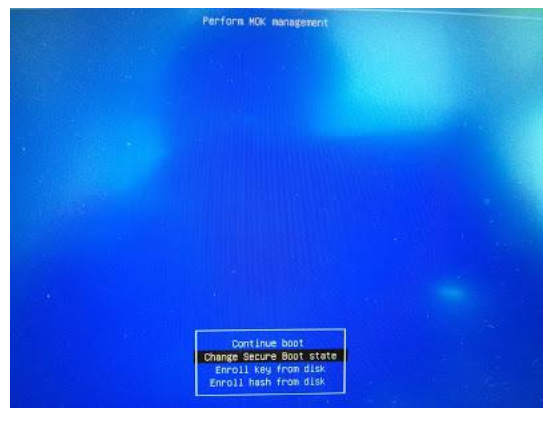
Enter the password you had selected in Step 2 and press Enter.
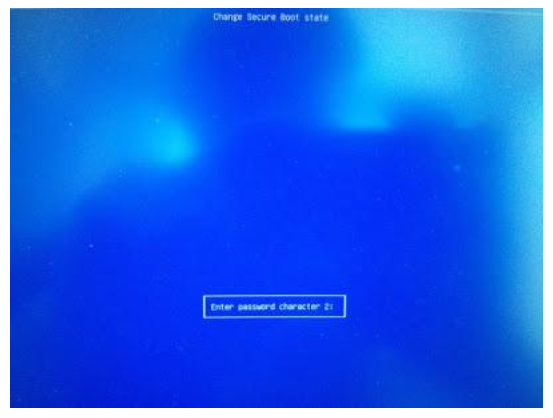
Select Yes to disable Secure Boot in shim-signed.
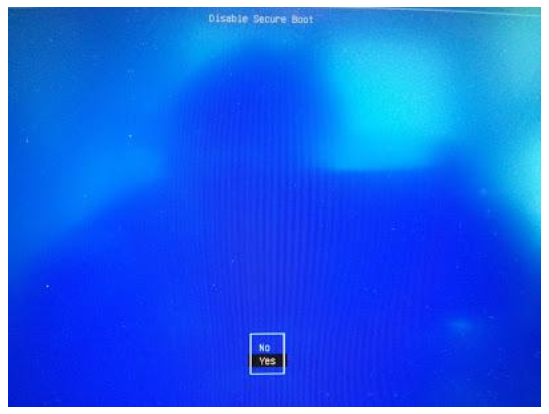
Press Enter key to finish the whole procedure.
To re-enable Secure Boot validation in shim, simply run sudo mokutil --enable-validation.
Method 3 - Disable Secure Boot from BIOS
- Enter BIOS setup
- Disable secure boot
- Save configuration
- Reboot the system
Manual method
You may also opt to sign modules yourself. To make this simple, you can use the command:
sudo update-secureboot-policy --new-key
To create a new MOK key to use for signing, then run the appropriate kmodsign command to sign your kernel module. After the module is signed, run sudo update-secureboot-policy --enroll-key to step through the enrollment wizard, or do the enrollment yourself by running sudo mokutil --import <your key>.
UEFI/SecureBoot/DKMS (last edited 2018-06-26 19:53:49 by cyphermox)