DKMS
DKMS do not work on systems with Secure Boot enabled
Following an UOS approved spec, Ubuntu is checking module signing by default, on kernels 4.4.0-18.34, 4.4.0-21.37, 4.2.0-42.49, 3.19.0-65.73 and 3.13.0-92.139 onwards.
Because of those changes, DKMS modules will not work on systems with Secure Boot is enabled.
In order to make DKMS work, Secure Boot needs to be disabled. There are several methods to disable Secure Boot in your system:
Method 1 - Disable Secure Boot from BIOS
- Enter BIOS setup
- Disable secure boot
- Save configuration
- Reboot the system
Method 2 - Disable Secure Boot in shim-signed
Open a terminal by Ctrl + Alt + T, execute sudo update-secureboot-policy and then select Yes
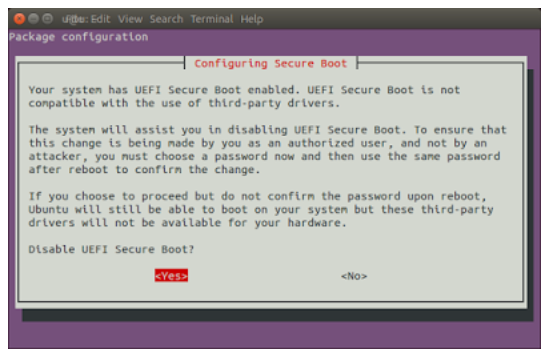
Enter a temporary password between 8 to 16 digits. (For example, 12345678, we will use this password later.)
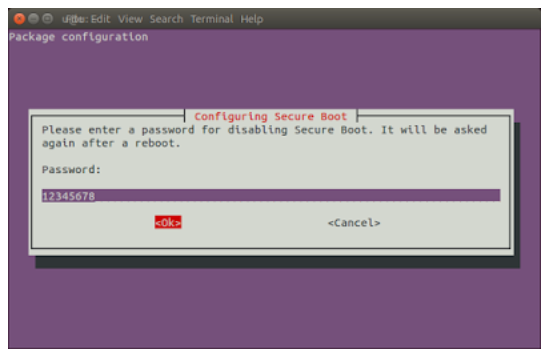
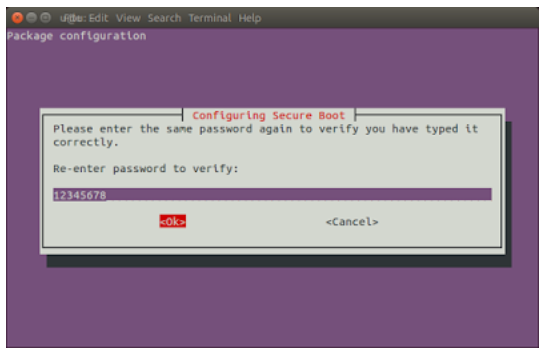
Enter the same password again to confirm
Reboot the system and press any key when you see the blue screen (MOK management)
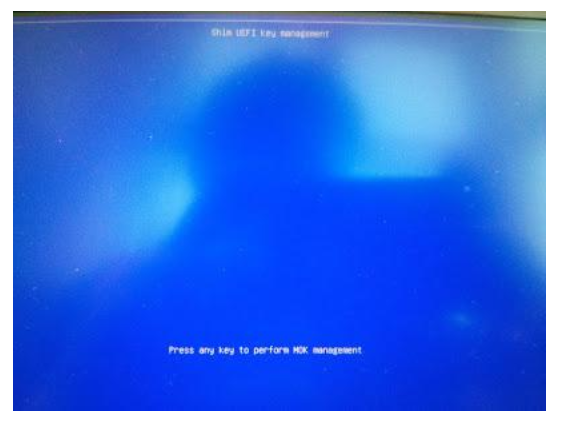
Select Change Secure Boot state
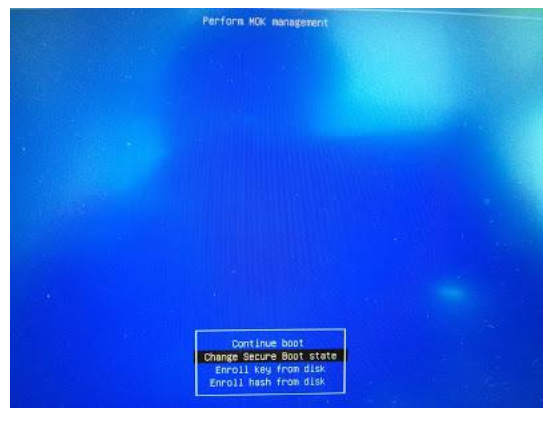
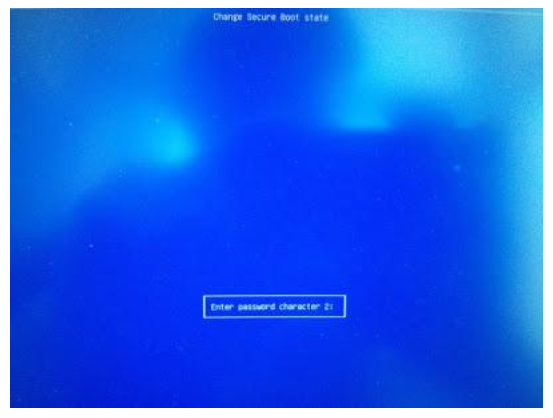
Press the corresponding password character and press Enter. Repeat this step several times to confirm previous temporary password like 12345678 in Step 2 and Step 3. For exmaple, 2 shown in below picture
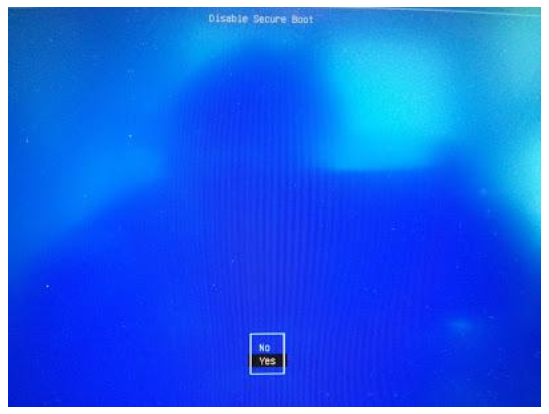
Select Yes to disable Secure Boot in shim-signed
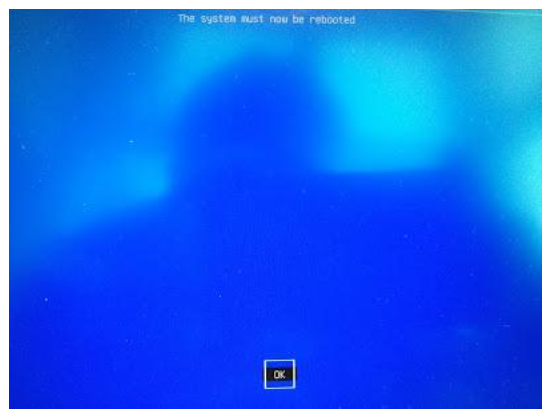
Press Enter key to finish the whole procedure
We can still enable Secure Boot in shim-signed again. Just execute sudo update-secureboot-policy --enable and then follow the similar steps above