DebuggingSecurity
Introduction
Marking an Ubuntu bug as a "security bug" (handled by the Ubuntu Security Team) means that the bug affects the security of the system in some way, resulting in a loss or degradation of security measures. Various categories might include:
- gaining privileges of another user without authorization. For example, a stack overflow in a setuid program allowing a regular user to become the root user. ("Privilege Escalation")
- accessing information that should be blocked. For example, a user on the system being able to view or modify private files of another user. ("Loss of Privacy")
- causing data-loss for another user. For example, a flaw in a database application allows a user to corrupt another user's stored information. ("Data Corruption")
- regression in security features. For example, if the default password hashing algorithm reverts to DES from md5. ("Regression")
- causing system services to become unavailable. For example, a network daemon can be taken offline remotely. ("Remote Denial of Service")
Marking an Ubuntu security bug as "private" is done in situations where a vulnerability is not yet publicly known. Attempts should be made to contact the upstream project (and other Linux Distributions) privately so that a "coordinated release date" (CRD) can be established. During this time, upstreams and Distributions can work to solve the problem before it goes public, in the hopes of heading off any public exploitation of the flaw. In situations where an upstream and Distributions are not interested in a CRD, the bug can made public so more developers can view the issue. (See "How to Forward" below for more details.)
All security flaws are assigned a CVE identifier. This is used to globally track the flaw so that other Distributions have a common identifier that can be used to discuss the flaw and its solution.
How to File
New security bugs should be created in the Ubuntu bug tracker (Launchpad). If you do not have a Launchpad account and prefer not to create one, you may send your report to security@ubuntu.com.
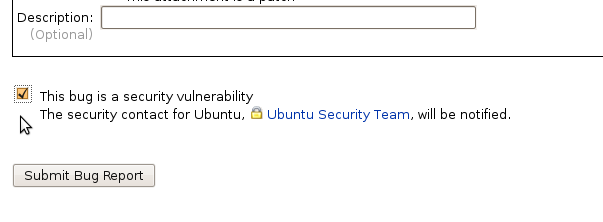
To report a security vulnerability in an Ubuntu package, follow the regular bug-filing instructions, but take special note of the "Mark as security issue" check box near the bottom of the form:
|
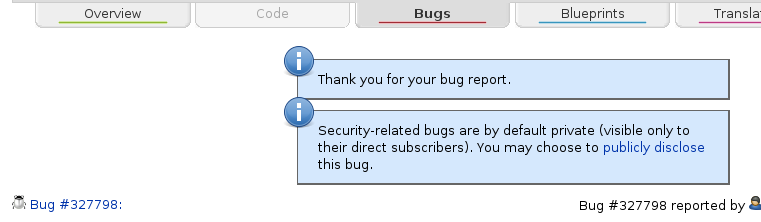
By default, all security bugs start their life marked as "private". If the security issue is already public (e.g. in another public bug tracker, discussed on a public mailing list, etc), please follow the "publicly disclose" link in the messages above the filed report:
|
In the privacy/security page, you can uncheck the "private" flag, and save the bug:
|
As with all bugs, please include as much information as possible, including the steps to reproduce the issue starting from a stock installation. In some more complex situations, it can help to carefully explain the difference between the expected results and the unexpected results. (There are many applications in Ubuntu, and most developers do not have familiarity with all of them.)
Subscriptions, Assignments, and Tags
Security bugs automatically have the "ubuntu-security" team subscribed. If the report is against a package in the "universe" repository, it can help with triage to subscribe the "motu-swat" team. This is especially true for private bugs, where there is already a very small audience available to triage bugs.
Please do not assign any team to a bug -- this is only done for MIR Audit requests. Subscriptions are sufficent to get the attention of needed teams.
Tags are used to help track specific classes of bugs or wishlist items. Please use the following tags to identify certain situations:
"hardened-ftbfs" When a package does not build due to the hardened CompilerFlags, and a solution is not immediately known, please add this tag.
- "format-security" When a package's build log shows *printf format security warnings ("warning: format is not string literal"), and needs attention to fix possible issues.
- "missing-nx" When a package is built where a program's stack is needlessly marked executable. This tends to happen when there is direct assembly being compiled in and it lacks the stack non-execute bits.
If there are other classes of bugs to track with tags, please discuss them with the SecurityTeam first.
Triage
Known Bugs
Many security issues are tracked only by their CVE identifier and may not yet have an Ubuntu bug opened for them. The Ubuntu CVE tracker contains the list of open security issues for packages in main/restricted and for universe/multiverse.
For completeness, the list of all CVE identifiers can be reviewed.
Non-Bugs
- What are Ubuntu's security policies?
Many common issues come up that may seem to be security design problems, but are actually done intentionally. Please review the Ubuntu Security Policies.
- How do I write secure software?
- There is no single answer, but some good resources are:
David Wheeler's Secure Programming for Linux and Unix HOWTO -- Creating Secure Software (fantastic to start with)
Mozilla's secure web coding guidelines
The Art of Software Security Assessment: Identifying and Preventing Software Vulnerabilities
A Bug Hunter's Diary: A Guided Tour Through the Wilds of Software Security
CERT's C Coding Standard
- There is no single answer, but some good resources are:
GPG Keys used by Ubuntu
- What GPG keys are used to verify Ubuntu distributions?
The Ubuntu Archives are signed with keys:
pub rsa4096/871920D1991BC93C 2018-09-17 [SC] F6ECB3762474EDA9D21B7022871920D1991BC93C uid [ unknown] Ubuntu Archive Automatic Signing Key (2018) <ftpmaster@ubuntu.com> pub 4096R/3B4FE6ACC0B21F32 2012-05-11 Key fingerprint = 790B C727 7767 219C 42C8 6F93 3B4F E6AC C0B2 1F32 uid Ubuntu Archive Automatic Signing Key (2012) <ftpmaster@ubuntu.com>The Ubuntu ISO Images are signed with keys:
pub 1024D/FBB75451 2004-12-30 Key fingerprint = C598 6B4F 1257 FFA8 6632 CBA7 4618 1433 FBB7 5451 uid Ubuntu CD Image Automatic Signing Key <cdimage@ubuntu.com> pub 4096R/EFE21092 2012-05-11 Key fingerprint = 8439 38DF 228D 22F7 B374 2BC0 D94A A3F0 EFE2 1092 uid Ubuntu CD Image Automatic Signing Key (2012) <cdimage@ubuntu.com>The Ubuntu Cloud Images checksums are signed with key:
pub 4096R/7DB87C81 2009-09-15 Key fingerprint = D2EB 4462 6FDD C30B 513D 5BB7 1A5D 6C4C 7DB8 7C81 uid UEC Image Automatic Signing Key <cdimage@ubuntu.com>The Ubuntu Cloud Images simplestreams are signed with key:
pub rsa4096 2012-10-27 [SC] 4A3C E3CD 565D 7EB5 C810 E2B9 7FF3 F408 476C F100 uid Ubuntu Cloud Image Builder (Canonical Internal Cloud Image Builder) <ubuntu-cloudbuilder-noreply@canonical.com> sub rsa4096 2012-10-27 [E]The ddebs debug package repositories are signed with key:
pub 4096R/5FDFF622 2016-03-21 [expires: 2021-03-20] Key fingerprint = F2ED C64D C5AE E1F6 B9C6 21F0 C8CA B659 5FDF F622 uid Ubuntu Debug Symbol Archive Automatic Signing Key (2016) <ubuntu-archive@lists.ubuntu.com> pub 1024D/428D7C01 2008-09-02 Key fingerprint = 2512 191F EF87 29D6 E5AF 414D ECDC AD72 428D 7C01 uid Ubuntu Debug Symbol Archive Automatic Signing Key <ubuntu-archive@lists.ubuntu.com> sub 2048g/A2C2A7A5 2008-09-02The Kernel PPA packages are signed with key:
pub 2048R/17C622B0 2008-05-01 Key fingerprint = 60AA 7B6F 3043 4AE6 8E56 9963 E50C 6A09 17C6 22B0 uid Kernel PPA <kernel-ppa@canonical.com>The Ubuntu Archive Master key, used for Signing key rotations is:
pub rsa4096/0x0BFB847F3F272F5B 2007-11-09 [SC] Key fingerprint = 153F 1C9E F139 5FBF 0035 2E8D 0BFB 847F 3F27 2F5B uid Ubuntu Archive Master Signing Key <ftpmaster@ubuntu.com>The Ubuntu Extended Security Maintenance archive is signed with:
pub rsa4096/67C7A026 2017-04-21 [SC] Key fingerprint = 74AE 092F 7629 ACDF 4FB1 7310 B4C2 AF7A 67C7 A026 uid Ubuntu Extended Security Maintenance Automatic Signing Key <esm@canonical.com> uid Ubuntu ESM <prodstack-cdo@canonical.com> sub rsa4096/80EE65B3 2017-04-21 [E]The Ubuntu FIPS archive is signed with:
pub rsa4096/8D13028C 2017-01-09 [SC] Key fingerprint = A166 8774 12DA C26E 73CE BF3F F6C2 8017 8D13 028C uid Launchpad PPA for ubuntu-advantageThe Canonical OEM Vendor Archives are signed with key:
pub rsa2048 2008-08-07 [SC] 236252602787D6BDC2336849F9FDA6BED73CDC22 uid [ unknown] Canonical Archive Automatic Signing Key <ftpmaster@canonical.com>
Contact
- How can I contact the Ubuntu Security team about issues that are already publicly disclosed?
- Public discussions can take place in the following locations:
#ubuntu-security on irc.libera.chat (publicly logged),
by reaching out directly to security@ubuntu.com .
- Public discussions can take place in the following locations:
- How should private security issues be reported?
The preferred method of reporting a security issue is through Launchpad. Launchpad offers a "Private Security" mode that will only be visible to members of the security team and select administrators. Note that Launchpad will send an unencrypted mail with the contents of the bug report to the reporter. If this is not desired, a direct email can be sent.
All security team members can be reached at security@ubuntu.com. GPG can be used to encrypt these messages. Please use the following key:
Name
Key ID
Key Fingerprint
4072 60F7 616E CE4D 9D12 4627 98E9 740D C345 39E0
Please also see our disclosure and embargo policy
Additionally, the GPG key ids for the security team members can be found on their individual Launchpad pages which are linked to on the security team's page. We will keep this list of keys updated as needed:
Name
Key ID
Key Fingerprint
50C4 A0DD CF31 E452 CEB1 9B51 6569 D855 A744 BE93
EDC4 830F BD39 AB6A C510 47FB 052F 3670 18D5 C3D8
4150 10F1 BA23 C8C7 20DF B1F5 F321 7259 9D8D 2E97
44DF FFE4 C1A0 08E8 3229 E205 611F BDEC D594 6E0F
7FE7 9B44 5728 C8EA 0042 839E 45BC E75B 840B 1F69
8386 336B 1A31 0661 7381 5BE2 98F3 0077 28F0 6B7C
9027 4443 94FA 0EEB 52BD E0B2 6D4A 7990 BDE2 CC66
4EA3 825A D96C 4A31 335B B054 CD43 2CBF 7079 04EC
F763 837E FAF2 4ADB F356 7E5A 0DC9 8647 D37D 791E
8F06 E0BA C079 6B7E D5A3 63D2 538B 7C0D CCB5 A3C9
62BC A077 1D46 0DE7 3D4D 5F04 6741 9E45 C339 9EDD
7317 6FE2 0082 13C5 BD9E BB79 6B5F 8F2F E775 FC48
0382 7EEE 014E 2DAC 02CC 74F2 EDD0 EA1F DFCF E8FA
9B69 3D74 4080 2E8A 6FF8 03DE 1349 8F03 2CCF E9DA
B35E BCD3 5C67 17BC 0ADE B08A EC87 3ACE D468 723C
D968 2DBE 6C26 7206 8404 B967 080B CAD5 0BC3 E920
00F6 164E 9C2D 21BA FBC4 7E0E 58DA D120 A693 9167
A3A5 5CBD 534E 85F9 6B33 C3C6 46D9 8A9C 81D6 DFDE
842F 72F5 7740 1503 C2BD 85DC 8469 9748 68A4 9E75
E6B9 3048 B0BD 9EDA BCE3 0DFD EC3B 6B6A 6F60 C8C3
DBE9 37BD 8468 F721 CD47 59A7 C660 2BC7 B86A 3ED0
05C3 18FA 7C12 D826 3BD6 C516 738B DD02 ABDD 96C6
7C87 9CFE E766 6FEB 92D1 9CCF 33D6 780C 08BD 8BCD
71FB F17B E7E5 2D0C 2A2C 9144 F0B6 1460 B04C 4B56
CA76 B8FF 6BEE F559 25BE 3A65 27BC 4FFA 4459 39B8
DBAC A8CC 694B BD8F 0F2E 64BD 0BE7 6EF9 F3A3 884C
AEE1 7FB5 A55E 0900 0C57 E8FB 199C 5BF4 DFD6 0328
4C1F E720 3CBD 9EF0 9280 0523 DE05 D098 EFD3 AF7C
2B1C 3DC8 E80A A9A9 FBFE 4FB6 703A AD91 046C D76E
77A8 B91B 62C9 FE75 F70F 6F82 A3BF F616 8D21 7C0C
91DF 7C99 D15C 9D07 4FEE F424 B86A EDCE 8B7B A4E7
B7C2 A106 6F3E 7C3B 03F6 9594 635C 65FF 1ED4 BA87
B203 D9C0 E11E 6265 8015 CC5A E02C CF71 9653 F2E4
0B76 30B2 A7E6 6D8F B18F 466C 3E3A 8051 6A22 B394
95D9 DED1 53BE 79BA D4A7 C773 BB05 ADC4 298B 2829
F389 8AB3 3FCF 5009 FB61 7FB2 AA11 2B18 F162 8D3F
38C7 7D33 8569 73A5 8762 FBFE 401E FCBC DA0F F1BD
1CD4 F909 1C5D 9AD8 3ABD 0B00 E37D 9730 0299 84CB
2CE2 D764 4158 4077 1258 41E2 C9F5 B69B D2DD BBAB
C8C0 C739 31B4 607E 54B1 A8C8 F294 8255 0658 1F28
07F8 317F B77C 09DD 8E2A 1A89 B6F2 490E 12CC DC93
A3F9 30E3 0D41 1990 6E5C 7DCE 3BAF 7D5D 0EF9 A4AA
D8B0 2037 006E 0E94 0C20 1709 AB9F D624 CA6A 421D
Group key receival:
gpg --keyserver keyserver.ubuntu.com --recv-keys 6569D855A744BE93 052F367018D5C3D8 F32172599D8D2E97 611FBDECD5946E0F 45BCE75B840B1F69 98F3007728F06B7C 6D4A7990BDE2CC66 CD432CBF707904EC 0DC98647D37D791E 538B7C0DCCB5A3C9 67419E45C3399EDD 6B5F8F2FE775FC48 EDD0EA1FDFCFE8FA 13498F032CCFE9DA EC873ACED468723C 080BCAD50BC3E920 58DAD120A6939167 46D98A9C81D6DFDE 8469974868A49E75 EC3B6B6A6F60C8C3 C6602BC7B86A3ED0 738BDD02ABDD96C6 33D6780C08BD8BCD F0B61460B04C4B56 27BC4FFA445939B8 0BE76EF9F3A3884C 199C5BF4DFD60328 DE05D098EFD3AF7C 703AAD91046CD76E A3BFF6168D217C0C B86AEDCE8B7BA4E7 635C65FF1ED4BA87 E02CCF719653F2E4 3E3A80516A22B394 BB05ADC4298B2829 AA112B18F1628D3F 401EFCBCDA0FF1BD E37D9730029984CB C9F5B69BD2DDBBAB F294825506581F28 B6F2490E12CCDC93 3BAF7D5D0EF9A4AA AB9FD624CA6A421D