OneiricDesktopNetworkEnhancementsSpec
Launchpad Entry: desktop-o-desktop-network-enhancements
Created: 2011-05-24
Contributors: mathieu-tl, jdstrand, broder
Packages affected: network-manager, network-manager-gnome, indicator-network
Summary
This is somewhat of a catch-all for the most important features that we wish to land to improve usability of NetworkManager. Adding proxy and firewall support were discussed at UDS-O, and so was IPv6 (briefly) in this spec, and a little more in detail in the IPv6 health-check spec.
Release Note
A number of enhancements to NetworkManager have been done in Oneiric. In particular, IPv6 addresses are now requested by default, although their presence remains optional to bring up an interface. Proxy and firewall configuration support, integrated with an user's connection to form per-network "profiles" have been added. Firewall and proxy are off by default.
Rationale
It's getting more common to require proxy configurations in some environments to access the Internet; and doing proxy configuration manually when the network location changes tends to be cumbersome.
Host-based firewalls are very common in Windows environments, and increasingly more common on Linux as the myths of being "unbreakable" and virus-free vanish. Furthermore, IPv6 support brings back the requirement of using host-based firewalls due to the somewhat direct access of systems to the Internet via autoconfiguration; which makes network-wide firewalling complex.
User stories
Bob needs to use a proxy at work to browse the web, yet doesn't use one at home. Right now he has to manually bring up the proxy configuration dialog and change his settings, remembering to change them back when he's in the other location.
John is worried about the security of his data. He runs a webserver on his system and SSH to share files with his coworkers and connect to his system remotely from within the office, but he doesn't want those to be exposed to the internet when he is at home. He uses ufw which he has to remember to turn off and on when he changes locations.
Marc shares his music with his family when at home. He wants a firewall configuration while at home that allows this and a different firewall configuration while at the coffee shop that does not.
Assumptions
Firewall support: as a first pass we'll assume the simplest possible settings to be exposed to the users. What this means is providing a way to turn on or off the firewalling on a per-network basis, and exposing presets from UFW to open specific applications.
Proxy support: GNOME already has the concept of profiles for proxy settings. We can safely assume it sufficient to match profiles to connections as a 1:1 relationship, and making sure we keep a "default" proxy setting which enables to proxy.
Design
Proxy settings already exist in System Settings. Ubuntu should not have multiple interfaces to proxy settings.
Second draft of a firewall settings design:
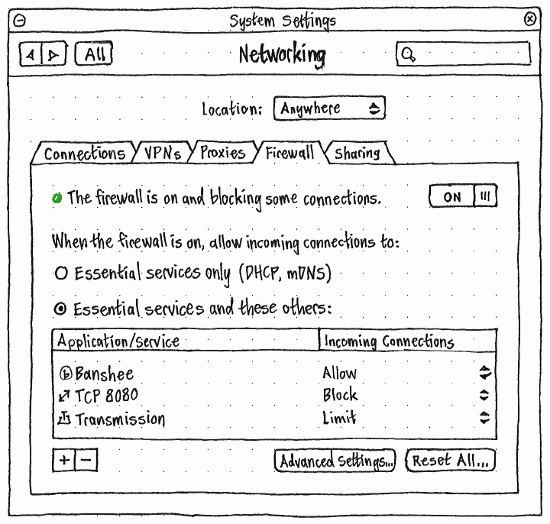
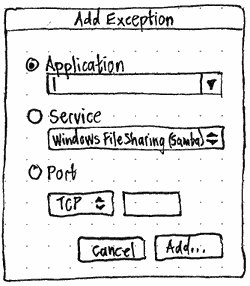
Questions that could alter this design:
Does System Settings have a Security panel? If so, maybe this should move there, but with a button here linking to it. not yet
How long does the firewall take to start or stop? (0.1 seconds? 2 seconds? 10 seconds?) near-instantaneous
Does stopping the firewall involve interrupting any current connections? don't think so, not unless they should be blocked
- Is blocking outgoing connections at all useful enough to show at the top level like this?
yes - why (asked by jdstrand)?
[jdstrand]: no. Here's why:
- user is not in a position to make an informed decision on whether the application should go onto the internet (so much of the desktop reaches out to the internet)
- iptables no longer supports rules by executable, so saying 'applications or services' is somewhat misleading
- it is conceivable to use 'owner' (for uid/gid), but this doesn't work well in this capacity
Does Ubuntu have any “essential” incoming connections? (Mac OS X identifies “DHCP, Bonjour, and IPSec” as essential.) yes: dhclient, avahi, ping, etc. These are already accounted for in ufw when it is enabled so this check box is not needed.
Does Ubuntu have any “essential” outgoing connections? Need answer from security team. Web browsing, e-mail, Avahi? - yes, everything (see above)
Are firewall settings per connection useful? yes, this allows having a strict firewall at the coffee shop and a more lenient firewall while at home
Comments from security team:
- Requirements as seen by jdstrand:
- turn on or off the firewall
- add incoming port/applications
- have firewall settings by connection (which allows for home, coffee shop, work, etc)
- allow from ip address/network. Alternately, have a simple check box that is 'Allow all from this network' which network manager is smart enough to figure out the network to give to ufw
- Comments on current design:
- Allow incoming connections to 'Any application or service' creates an open firewall. This can sometimes be useful, but is not the most clear way to convey this, and is not what people want when they 'enable a firewall'
- Allow incoming connections to 'Essential services only' also adds complexity. If the services are essential, why would we block them? ufw already handles them any way, and if someone wants to disable them, that is a special configuration that people can change in /etc/ufw/before*.rules
- As mentioned, egress filtering is not desired in the gui. It is very error prone and requires a high degree of skill to properly configure. You also cannot restrict by application so while we can say 'allow to ports 80/tcp and 443/tcp), saying in the gui 'allow web browsing' implies that only firefox can browse, when in actuality any application can browse.
This specification is now complete at https://wiki.ubuntu.com/Networking#Firewall
Implementation
UI Changes
Should include one extra page per "feature": may be tabs, one "Proxy", one "Firewall", and expose as few settings as possible to make it really simple to configure (or ignore).
Code Changes
Discussed proxy implementation with Dan Williams (dcbw). Proxy support will require keeping track of proxy settings in an object such as NMSettingsProxy. It may be necessary to get at least WPAD, which is already retrieved from DHCP, to integrate into this (since it's proxy auto-detection). This would likely end up an additional section in the configuration file:
[proxy] profile=Home
Firewall implementation would likely rather be done as a plugin, since it's very distro-specific. In our case, using UFW, speaking in DBUS to UFW to turn on or off firewalling and choosing settings (or choosing a specific profile at the UFW level, pending implementation there).
Migration
There is no previous data to migrate. Users will be presented with extra tabs which should make the configuration both discoverable, and very much out of the way from those who don't need it.
Test/Demo Plan
It's important that we are able to test new features, and demonstrate them to users. Use this section to describe a short plan that anybody can follow that demonstrates the feature is working. This can then be used during testing, and to show off after release. Please add an entry to http://testcases.qa.ubuntu.com/Coverage/NewFeatures for tracking test coverage. This need not be added or completed until the specification is nearing beta.
Unresolved issues
This should highlight any issues that should be addressed in further specifications, and not problems with the specification itself; since any specification with problems cannot be approved.
BoF agenda and discussion
#uds-o #track #topic
What should we have in NetworkManager?
* discussion about integrating firewall profiles into NM
* UFW does not support profiles, but can be added
Upstream is dropping nm-applet, moving to gnome-shell
* first option is to for nm-applet
* second option is move to network-indicator, with NM as backend, and add UFW as an extension
UFW profiles
* home - trust all machines on the network
* not home - other case
* per connection network setting?
- e.g on wired, always enable firewall; on wireless XYZ, enable firewall, on wireless ZYX, disable firewall
-different proxy settings for different connections.
1st pass:
- enable/disable
- ports/application profiles
- alpha 1 on and off
- [ACTION] jdstrand - add profile support by alpha 2
Possibly:
- on or off depending on connection
- profiles per connection (network manager doesn't have it)
- default profile
- profile based on the connectionOneiricDesktopNetworkEnhancementsSpec (last edited 2011-08-05 15:24:29 by mpt)